Interfaces.
Let's look at the flow.
Packet comes in.
The Firewall determines which zone it is coming from based on the interface it is on.
The firewall looks at the Packet Forwarding table
The Firewall determines which ZONE it will go out to
Interface modes.
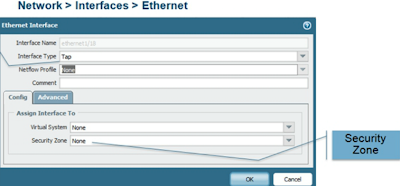
TAP
This mode is useful for conducting a Proof of Concept and gaining visibility
it requires no change.
You only have to create a SPAN port on a switch and funnel a copy of the packet to the firewall.
The configuration is like this.
So the interface type : TAP
Netflow :
CONFIG here you can assign the interface to a VSYS you can also select the security zone.
When you set up policies later in order to test them, the source will be that zone and the same with the destination. That is the workaround so the Policy is logged.
vWIRE
Protection yes,
Decryption yes
NAT yes
-This will bind TWO physical ports together {in and out}
No MAC no IP is given to the address.
VPN will not be able to terminate on this device...... NO VPN
Steps:
Create a Virtual Wire Object.
Add interfaces to the object.
Creating the OBJECT.
Give it a name
Add interfaces to it.
Select which VLANS to allow on it. 0 zero = untagged.
OK, the interfaces need to be created first or after you create the object, it's up to you.
So type : vWIRE
Assign to OBJECT, which would be the one we created above.
Assign to a security zone. This will be used later for the policy creation.
Anyway, vWIRE is a physical interface to another physical interface.
The name is usually a bump in the wire or transparent firewall.
Layer 3 mode - enterprise firewall
If you use Routing or NAT or VPN
You must set up the L3 mode.
Require
IP address
ZONE the itnerface will belong to
Virtual Router it will use.
all layer 3 interfaces in the same virtual router will share the same routing table.
The layer 3 interfaces can be manual or using a DHCP client
The Layer 3 interface can be given access to the management so you can use them to connect to the device.
NAME
Type: Layer 3
Virtual Router it belongs to - routing table
Virtual system VR
Security zone it will belong to - untrusted
Select IP static or IP DHCP client.
Advanced tab contains the Link speed , state
TUNNEL
This is a logical layer 3 interface.
Anything that says send it to the Tunnel will be send to that tunnel which will use the IPSEC object associated with it.
Tunnel.
Virtual router it belongs to so it can go on that routing table.
Security zone of the interface. _ untrust in this case.
There is a LITTLE 1 at the corner that is the tunnel identifier
this is a numerical identifier.
On a layer 3 interface we can allow you to access the management items.
Like manage the interface, ping it , get snmp etc.
You basically create a management profile.
Then you go to the interface and in the ADVANCED tab.
You apply that management profile.
Other info.
In a few years it will be in the other other other info. That is why I prefer better structure but I guess Firewall people do not care.
Subinterface.
Layer 2
Ok, subinterface ID. try to make it match the VLAN.
TAG , which TAG to put on the vlan.
Virtual system
Security zone
This is baiscally a SVI a RVI a VLAN with a L3 IP address.
So,
Interface and Subitnerface ID.
Try to make it match the VLAN which is the TAG
Select the virtual router so it will be placed in the routing table.
Select the TAB IPv4 and give it an address
Then finally select a security zone.
Last but not least,
Loopback.,
You can create a loopback, this is usefull for troubleshooting and routing protocols.
Security Zones
Policies use ZONES to regulate traffic.
INTRA ZONE Allowed
INTER ZONE Denied
Each TYPE of port must have a separate zone.
So a L2 port will have one zone
a L3 will have another
The TYPE of port must match in order to create a policy.
An Interface MUST belong to a zone before it can process any traffic.
Interface can belong to one zone only.
A security zone can have many interfaces.
A logical interface can belong to ONE zone only.
GUI will not allow you to assign an interface that is the wrong type.
* TAP
* Virtual Wire
* Layer 2
* Layer 3
* External zone. - This is used to transfer between different Virtual Systems on the same firewall.
A policy is from ZONE to ZONE it does not care about the interfaces.
Wednesday, May 29, 2013
Wednesday, May 15, 2013
Introduction to Palo Alto
Hello,
Let's have a look at Palo Alto.
Why, how to cut through the fluff and passing the ACE exam.
Let's start, why ?
As you can see or if you don't know the Magic Quadrant (TM) from Gartner is basically a measure
of how well companies are doing when compared to other companies.
Visionaries are those with new cutting edge technologies.
Leaders are companies that deliver large numbers and hold a more dominant position.
Challengers means they have some potential
and niche means somebody is buying them.
This quadrant is for the ENTERPRISE not the SMB. So you won't see loads of cheap
ASAs or sonicwalls affecting the chart.
Let's see why.
Check point took the lead back in 1994 and has led it consistently.
They came up with the VPN, they came up with centrally managing firewalls using a centralized device.
Palo Alto has just caught up.
They have the same level Firewall
They have the VPN
They have the Panorama which is the centralized management appliance.
They also have
WildFire - which allows you to protect against zero day attacks.
Application visibility - which allows you to view into applications to see nested applications {like chat}
Streaming- they claim they can scan the file as it is being streamed across and don't need to
buffer the whole file before starting to check it.
So as you can see, they basically have the same as Checkpoint and some added features.
The second reason they have catapulted this much is Checkpoint.
Their manager is notoriously cheap in his compensation to employees.
That is why ZUK {the CTO of Palo Alto} left him.
That is why their staff retention is low.
So their support is lacking and causes people to move away from them.
The above is what I have personally heard from disgruntled ex-employees so of course you can take it with a grain of salt.
So,
Fortinet, Juniper, Cisco, Sonicwall are all nice firewalls PER firewall
but do not have the centralized policy capabilities that Palo Alto and Checkpoint mainly have.
There you are.
As you can see Palo Alto is here to stay and clients are actually demanding we sell it to them.
Studying about Palo Alto.
Resources you can use are.
1. Support Portal http://support.paloaltonetworks.com
*this resource requires a serial number in order to get a username.
that is a challenging regulation. So if you are a partner you can see if they will bypass the rule.
2. Palo Alto Education portal http://educations.paloaltonetworks.com
* this resource requires you be a partner.
Both in tandem should give you the tools to pass the exam.
The first part is the .
101 training. "Firewall configuration essentials 101 PAN-OS v.5.0
Alternatively you can go to a class called EDU-201 which is an instructor based class.
Both will have labs for you. In order to do the labs, you must have access to the hardware.
The cheapest firewall is not very cheap so try for the NFR which is also not cheap or just memorize the labs.
The last items are
ACE study guide - useless
Palo-Alto 4.1 administrator Manual. - useless.
In general you will the company is new so the documentation is all over the place.
The GUI on the device is also al over the place and not really as consistent and logical as an apple device
or even a Juniper for that matter.
Let's have a look at Palo Alto.
Why, how to cut through the fluff and passing the ACE exam.
Let's start, why ?
As you can see or if you don't know the Magic Quadrant (TM) from Gartner is basically a measure
of how well companies are doing when compared to other companies.
Visionaries are those with new cutting edge technologies.
Leaders are companies that deliver large numbers and hold a more dominant position.
Challengers means they have some potential
and niche means somebody is buying them.
This quadrant is for the ENTERPRISE not the SMB. So you won't see loads of cheap
ASAs or sonicwalls affecting the chart.
Let's see why.
Check point took the lead back in 1994 and has led it consistently.
They came up with the VPN, they came up with centrally managing firewalls using a centralized device.
Palo Alto has just caught up.
They have the same level Firewall
They have the VPN
They have the Panorama which is the centralized management appliance.
They also have
WildFire - which allows you to protect against zero day attacks.
Application visibility - which allows you to view into applications to see nested applications {like chat}
Streaming- they claim they can scan the file as it is being streamed across and don't need to
buffer the whole file before starting to check it.
So as you can see, they basically have the same as Checkpoint and some added features.
The second reason they have catapulted this much is Checkpoint.
Their manager is notoriously cheap in his compensation to employees.
That is why ZUK {the CTO of Palo Alto} left him.
That is why their staff retention is low.
So their support is lacking and causes people to move away from them.
The above is what I have personally heard from disgruntled ex-employees so of course you can take it with a grain of salt.
So,
Fortinet, Juniper, Cisco, Sonicwall are all nice firewalls PER firewall
but do not have the centralized policy capabilities that Palo Alto and Checkpoint mainly have.
There you are.
As you can see Palo Alto is here to stay and clients are actually demanding we sell it to them.
Studying about Palo Alto.
Resources you can use are.
1. Support Portal http://support.paloaltonetworks.com
*this resource requires a serial number in order to get a username.
that is a challenging regulation. So if you are a partner you can see if they will bypass the rule.
2. Palo Alto Education portal http://educations.paloaltonetworks.com
* this resource requires you be a partner.
Both in tandem should give you the tools to pass the exam.
The first part is the .
101 training. "Firewall configuration essentials 101 PAN-OS v.5.0
Alternatively you can go to a class called EDU-201 which is an instructor based class.
Both will have labs for you. In order to do the labs, you must have access to the hardware.
The cheapest firewall is not very cheap so try for the NFR which is also not cheap or just memorize the labs.
The last items are
ACE study guide - useless
Palo-Alto 4.1 administrator Manual. - useless.
In general you will the company is new so the documentation is all over the place.
The GUI on the device is also al over the place and not really as consistent and logical as an apple device
or even a Juniper for that matter.
Subscribe to:
Posts (Atom)