Interfaces.
Let's look at the flow.
Packet comes in.
The Firewall determines which zone it is coming from based on the interface it is on.
The firewall looks at the Packet Forwarding table
The Firewall determines which ZONE it will go out to
Interface modes.
TAP
This mode is useful for conducting a Proof of Concept and gaining visibility
it requires no change.
You only have to create a SPAN port on a switch and funnel a copy of the packet to the firewall.
The configuration is like this.
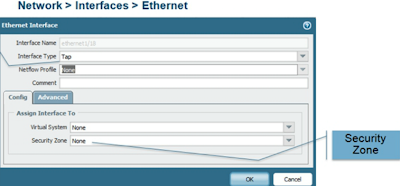
So the interface type : TAP
Netflow :
CONFIG here you can assign the interface to a VSYS you can also select the security zone.
When you set up policies later in order to test them, the source will be that zone and the same with the destination. That is the workaround so the Policy is logged.
vWIRE
Protection yes,
Decryption yes
NAT yes
-This will bind TWO physical ports together {in and out}
No MAC no IP is given to the address.
VPN will not be able to terminate on this device...... NO VPN
Steps:
Create a Virtual Wire Object.
Add interfaces to the object.
Creating the OBJECT.
Give it a name
Add interfaces to it.
Select which VLANS to allow on it. 0 zero = untagged.
OK, the interfaces need to be created first or after you create the object, it's up to you.
So type : vWIRE
Assign to OBJECT, which would be the one we created above.
Assign to a security zone. This will be used later for the policy creation.
Anyway, vWIRE is a physical interface to another physical interface.
The name is usually a bump in the wire or transparent firewall.
Layer 3 mode - enterprise firewall
If you use Routing or NAT or VPN
You must set up the L3 mode.
Require
IP address
ZONE the itnerface will belong to
Virtual Router it will use.
all layer 3 interfaces in the same virtual router will share the same routing table.
The layer 3 interfaces can be manual or using a DHCP client
The Layer 3 interface can be given access to the management so you can use them to connect to the device.
NAME
Type: Layer 3
Virtual Router it belongs to - routing table
Virtual system VR
Security zone it will belong to - untrusted
Select IP static or IP DHCP client.
Advanced tab contains the Link speed , state
TUNNEL
This is a logical layer 3 interface.
Anything that says send it to the Tunnel will be send to that tunnel which will use the IPSEC object associated with it.
Tunnel.
Virtual router it belongs to so it can go on that routing table.
Security zone of the interface. _ untrust in this case.
There is a LITTLE 1 at the corner that is the tunnel identifier
this is a numerical identifier.
On a layer 3 interface we can allow you to access the management items.
Like manage the interface, ping it , get snmp etc.
You basically create a management profile.
Then you go to the interface and in the ADVANCED tab.
You apply that management profile.
Other info.
In a few years it will be in the other other other info. That is why I prefer better structure but I guess Firewall people do not care.
Subinterface.
Layer 2
Ok, subinterface ID. try to make it match the VLAN.
TAG , which TAG to put on the vlan.
Virtual system
Security zone
This is baiscally a SVI a RVI a VLAN with a L3 IP address.
So,
Interface and Subitnerface ID.
Try to make it match the VLAN which is the TAG
Select the virtual router so it will be placed in the routing table.
Select the TAB IPv4 and give it an address
Then finally select a security zone.
Last but not least,
Loopback.,
You can create a loopback, this is usefull for troubleshooting and routing protocols.
Security Zones
Policies use ZONES to regulate traffic.
INTRA ZONE Allowed
INTER ZONE Denied
Each TYPE of port must have a separate zone.
So a L2 port will have one zone
a L3 will have another
The TYPE of port must match in order to create a policy.
An Interface MUST belong to a zone before it can process any traffic.
Interface can belong to one zone only.
A security zone can have many interfaces.
A logical interface can belong to ONE zone only.
GUI will not allow you to assign an interface that is the wrong type.
* TAP
* Virtual Wire
* Layer 2
* Layer 3
* External zone. - This is used to transfer between different Virtual Systems on the same firewall.
A policy is from ZONE to ZONE it does not care about the interfaces.

















Great article thanks!
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteGood read and to the point.
ReplyDeleteExcellent content. Nice and clearly explained.
ReplyDeleteExcellent content. Nice and clearly explained.
ReplyDeleteExcellent content. Nice and clearly explained.
ReplyDelete