Well NO.
This is the Checkpoint Network Special Engineer.
Alright.
Certified Network Security Engineer - Courtesy of Palo Alto.
To be honest, i was hoping someone else had written a guide but no such luck.
A few random guys posted they passed it
and some random company or two mention they passed it.
If you are doing this to get ahead in life, I doubt you will.
The certification is unknown in the industry.
If you go on Indeed and type CNSE for the whole of the USA.
You'll get 48 hits and they will be for college of nanoscale science and engineering
and some other healthcare programs, but then again when I started in IT no one know what a CCIE is.
Now, if you recall.
In the beginning god made the earth etc
Well eventually he made the internet and it was insecure.
So your first firewalls to protect you were stateless and basically blocked ports.
Then your second firewalls were stateful and remembered to expect traffic back on some port.
Well Palo Alto, technically doesn't care about ports.
Palo Alto is not even stateful. It simply cares about APPLICATIONS.
Now you can have 20 applications running on port 80.
AIM, messenger, facebook, youtube, chrome, salesforce, etc.
Palo Alto will use their signatures to recognize the application so you can apply rules to
APPLICATIONS.
Besides Palo Alto which is trying to break the mold you have Juniper Mikonos/Mykonos/Secure web application something {they keep rebranding} but that is for another blog .
So.
CNSE
Wow, where do I start.
well. I have no idea.
I googled and couldn't find any sort of guide.
The best is CNSE 5.1 study guide which looks more like a cheat sheet than a guide.
The themes for the exam are.
Have skill and knowledge in these subjects:
- Administration and Management
- Network Architecture
- Security Architecture
- Troubleshooting
- User-ID
- Content-ID
- App-ID
- Panorama
- GlobalProtect
So, I'll start with Panorama.
CNSE001
You are a serious guy, 3 kids and a bugaboo.
You manage the security for a big realestate agency.
You have two or ten datacenters with many servers.
So in each datacenter you have a firewall.
Now
You can't spend all day logging into 10 datacenters to collect and correlate logs
Also you can't have a stable security policy at all 10 locations if all you do is copy
rules manually.
Imagine a new rule, deny sales access facebook after 11:00 pm.
The reason for that rule is you don't want people to drunk post.
So now you have to copy it 10 times to each firewall, not going to happen.
So for "serious" people you have a management platform called Panorama.
Now this platform is great.
You can now justify to a client why he has to buy Palo Alto, because Palo Alto has a management
platform, while Cisco has bobkes and Juniper is trying to fix their "junos space".
So what does Panorama do.
1. It accumulates the logs from the devices so you can correlate data centrally.
2. It centralizes the configuration of all the firewalls.
3. Centralizes the deployment of new firewalls.
You deploy it by using
1. Virtual Machine appliance - ESXi 3.5 or VM 1.0.6+
2. Appliance (M-100)
So let's start by viewing the appliances.
If ever you want pricing. Go to any site and there should be MSRP prices on each item.
PAN-M-100
|
M-100, 1TB RAID 1 storage (2 1TB RAID certified drives
preinstalled)
|
$10,000
|
PAN-M-100-4TB
|
M-100, 4TB RAID 1 storage (8 1TB RAID certified drives
preinstalled)
|
$15,000
|
So, since you have two sizes. The first logical assumption you can make is that the TB storage will depend on how many logs do you estimate you will have.
Unfortunately there is nothing on the partner portal to tell you how to size this.
So my recommendation is to by the first one.
Monitor the size of the drive increase over time and based on that you can make your "retention" and future sizing of future purchases.
Now, do I think 6TB of storage is worth $5,000. No.
So, we have the device M-100.
Now we need to license each of the firewalls we have.
The licensing starts at.
Unfortunately there is nothing on the partner portal to tell you how to size this.
So my recommendation is to by the first one.
Monitor the size of the drive increase over time and based on that you can make your "retention" and future sizing of future purchases.
Now, do I think 6TB of storage is worth $5,000. No.
So, we have the device M-100.
Now we need to license each of the firewalls we have.
The licensing starts at.
PAN-M-P-25
|
Panorama
central management software license, 25 devices or log collector for the
M-series
|
$10,000
|
PAN-M-P-100
|
Panorama
central management software license, 100 devices for the M-series
|
$25,000
|
PAN-M-P-1K
|
Panorama
central management software license, 1000 devices for the M-series
|
$75,000
|
So using MSRP. The lowest cost Panorama will be $20,000
10000 hardware
10000 licensing.
Wait, still not done.
You have to add the yearly support costs.
10000 hardware
10000 licensing.
Wait, still not done.
You have to add the yearly support costs.
PAN-SVC-4HR-M-100-P-100
|
4-Hour
Premium support year 1, Panorama M-100 100 devices
|
$7,350
|
PAN-SVC-PREM-M-100-P-100
|
Premium
support year 1, Panorama M-100 100 devices
|
$5,600
|
4 hour means within 4 hours of them determining the problem is the hardware they will send a replacement.
Premium just means Next business day.
CNSE002
So, lets break it up with some images.
Above is the Palo Alto M-100 appliance with 8 HD and the license.
sss
Above is the Palo Alto M-100 appliance with 8 HD and the license.
sss
CNSE003
Let's review the equipment.
There is 1 10/100/1000 port at the front. (9)
CNSE004

There is a console port at the front. (8)
There is a port not in use (10) future use maybe.
There are two ports in the back that are reserved for future use.
The power is in the back. Single power.
A neat feature.
This M-100 has a UID Unique ID this is a button (5) you press.
It will make the device LED blink. Then when you go to the other side of the rack you can easily recognize
the device and avoid unplugging the wrong this.
So let's summarize their slides.
Either Vmware or Appliance.
Licenses are required for the endpoint firewalls 25,100,1000 increments.
You can take a 25 license and convert the M-100 into a "collector" , this will help offload processing from the main M-100 in this scenario. {Slide CNSE001 references this}
Either Vmware or Appliance.
Licenses are required for the endpoint firewalls 25,100,1000 increments.
You can take a 25 license and convert the M-100 into a "collector" , this will help offload processing from the main M-100 in this scenario. {Slide CNSE001 references this}
Installation.
The device comes with the rack rails.
Either 4 post or 2 post and threaded or not.
If you have no idea what I am talking about.
Then try www.apc.com or www.tripplite.com
M-100 Vmware.
Here you can avoid paying $10000 per appliance.
Minimum.
Quad Core VM
4GB DRAM
ESX 4.1 each document they say something else, so double check and try it first before deploying.
remember, hard in training easy in combat.
2 TB maximum HD on the VM for logs.
Here you can avoid paying $10000 per appliance.
Minimum.
Quad Core VM
4GB DRAM
ESX 4.1 each document they say something else, so double check and try it first before deploying.
remember, hard in training easy in combat.
2 TB maximum HD on the VM for logs.
Security.
For both it is a Radius or local
Active / passive is the HA
Up to 1000 devices is the maximum.
For both it is a Radius or local
Active / passive is the HA
Up to 1000 devices is the maximum.
References
https://www.paloaltonetworks.com/content/dam/paloaltonetworks-com/en_US/assets/pdf/datasheets/panorama/panorama.pdf
Panorama hardware installation guide.
Templates.
https://live.paloaltonetworks.com/docs/DOC-4125
In Panorama.
Well, let's say you have 500 firewall and you want to replace the NTP server with a new IP.
So either you QTP {script using GUI} Perl it or use a "template"
Since Panorama is mainly for security administrators who are more GUI orientated
the template has been offered.
Templates control the NETWORK settings
For example I can configure the template DMZ_template

Now when ever I have a new router. I apply the template DMZ_template and I get a router
configured with the right interfaces.
Saved myself some time. So now I can go slack off and update my blog and learn something new.
Now I can totally add to that.
For example I can say on the WAN interface don't allow ping
on the DMZ don't allow telnet
etc.
Basically you bundle up all the settings. This way you don't have to repeat it every time which is an
action that is prone to errors.

s
an example of configuring the mgmt interface in the template.
How to create templates.
First, templates are supported in version 5.0 and later.
Option 1
Create a template as a place holder, commit, get new device, apply the template to the device.
Option 2
Create a template, assign devices, commit to the devices.
OK,
I'll switch a little
In the Palo Alto Portal you can get a Panorama training
Panorama Management Software 121 PAN-OS v.5.1
So let's try summarizing it.
Panorama PAN-OS v5.1
| Image |
text
|
High availability of centralized management. cetralized configuration and software maintenance allows you to configure once and share it among the devices. Centralized logging. HA can be done active/passive |
|
responsibility or geography |
|
You can aggregate logs from many devices into a central location. Management is done through templates, device groups, role based administration and update management. You can store configuration backups on Panorama. Panorama can be converted into a dedicated log collector. Updates and licenses can be managed and deployed centrally. |
|
Showing how Panorama gives you flexibility. |
|
< 10 you can use VM panorama <100 devices you are fine with 1 > 100 you should look into scaling it out the reasons are the log collection and geographical distances between collectors and firewalls. |
|
64 bit so you can add more memory to VM. ESXi 5.0 64 bit must be used The file is OVF and you downlaod it. A snapshot will return the system to what it was when the snapshot was taken. |
|
Only M-100 can do log collection. |
|
Panorama allows you the option to set up a collector group. The reason is that you can set up different storage retention and SNMP. |
|
TCP port 3978 |
|
and then send them to the firewalls. This allows you to download the updates once and do this in a central fashion. You can also apply licenses from a central location. |
|
Instead of seeing per device the reports. Panorama aggregates them which allows you to defend the whole network and correlate data. |
|
Dynamic Superuser - full access. Superuser read only - read only Panoarama administrator - can't create other admins Role based - more granular control. Local admin can only get Dashboard and Security policies access. |
|
192.168.1.1/24 admin admin |
|
You click on licenses -->retrieve license from This will activate the license. Later on you can add more licenses using the "activate feature using authorization code". |
|
You can enable which services will be enabled. Permitted IP range also helps. Need to add the Source Subnet of the admin PC |
|
Panorama --> managed devices. Or add them from the device. Firewall Setup --> device --> management |
|
Put them into your logical device groups Create templates. |
|
Like we said. Device > Setup > management > program settings. If you are managed by an HA pair, then add both of their IPs Panoramas should be accessible via the MGT interface. If you are not using the MGT interfaces then set up a route. enable buttons in Yellow, will allow Panorama to PUSH configurations. Policy and object can't be overriden. Local admin can override templates. |
|
Creating a Role.
Select Panorama to create a Role for Panorama. Select Device Group to create a role for the Firewalls. Enable - Read only - Disable. |
|
Now when you create the new user.
You select a radio button. Dynamic - these are built in. {Superuser} {Superuser - read only} {Panorama administrator- can't create other admins} or Role Based - which relies on the role you created above. |
|
When you set up a user, you have the selection
Of the "Authentication profile". You can use this or use an "Authentication sequence". The sequence will let you run through a list of authentication profiles. |
|
Password complexity is for all of the panorama admin accounts.
The password profile is per user. This is applied under the authentication TAB of the user you just created. |
|
Authentication profile can be that or
authentication sequence. SSH can be turned on. Role being Dynamic and Role based. Profile is the Role based progile. The password profile |
|
Pending commits can be seen by other Panorama administrators.
|
|
If you see a LOCK, that means someone else is working on that part of the configuration.
Click on it to see who. The location of the admin and which of the records are locked. |
|
Commit to Panorama
Commit template changes to devices Commit them to a device group. Commit then to a collector group. |
|
Commit to Panorama.
From Panorama push the configuration to Device groups Templates --> then apply to devices Collector groups. |
|
Filters allow you to limit who will it be applied on.
|
|
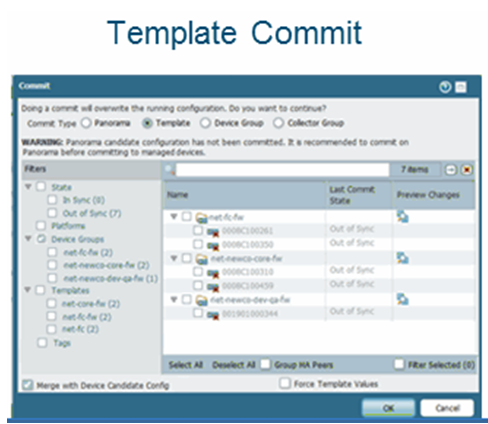
Merge with the candidate config
Force Template to override the local changes by the admin Include Device group + Network templates in a single commit |
|
This allows you to TAG a device with an administrative label. Like the location name, or something else.
This is only in the panorama and is not retained in the device itself. |
|
State will show if it is in sync or not.
Platform will be the device type. Device groups Templates members Tags You can press preview to see the propsed changes in the candidate config. Color coding. Green is added Yellow modified red -deleted |
|
Template commit.
This allows you to set the changes to the commit them to the template. |
|
Allows you the third item.
Committing to a group of devices. |
|
apply to a group of collectors....
|
|
Device Groups
|
|
Device group = logical grouping of devices.
Devices are added to the group. A device can belong to a single device group. Devices are either physical firewalls or virtual systems. |
|
The Shared group contains all of the device groups in it.
|
|
The GUI will look different till you create the first device group
|
|
Creating a device group.
Name Description - device group saar You select the firewalls on the right. You can use the filters to see less options. |
|
Alright,
Let's say you have a client - That client has an IP pool. 82.35.35.0/24 Now you want to create an object client002 = ip pool 82.35.35.0/24 Now you can use that in the firewall rules. If client002 to DMZ then allow. Now instead of creating this client in each of your 50 firewalls. You create a shared object in Panorama which will be pushed to all the firewalls. |
|
So, apparently each firewall has a different number of maximum shared objects.
For example small firewall = small number. Palo Alto recommends leaving the checkbox on "Share unused address ...." This won't send an object to a firewall if it is not in their policy. If you want to over-write objects that have the same name. Use "shared objects take precedence". This will over-write the local admins object {must be same name} |
|
This looks complex at first.
Remember, all the firewalls are in the SHARED group. So logically the first pre-policy is SHARED pre-policy. There you will put items all firewalls should allow, like DNS. remember you can logically split into "device" groups. Local firewall policies are done by local admin. SHARED post policy is simply any any deny! |
|
Panorama GUI configuring the
Panorama shared pre rules and post. Notice the context :Panorama: |
|
Zone names don't auto populate.
Zone names in the local firewalls are unknown to the Panorama. To make it easier, you can create zone names in the templates. This will allow them to auto populate. If you type a zone name manually a mistake in upper/lower case or letter will prevent the firewall from committing. |
|
Once you finish creating a policy.
You can push it to the "targets". If you want you can exclude devices or pick specific devices to target. As usual, you can use the filters to limit the choices. |
|
Preview rules will allow you to
see a preview of the accumulated rules. You can run this before applying the rules. Shared Pre Device group Local Post device group Post shared. |
|
This is another time the "Device group" commit.
You can filter and select specific firewalls. You can also merge Include device + Network templates and FORCE the template value.{overide local} |
|
Running a Device Commit to two VSYS on the same device will cause a fail firewall_51.
Each physical firewall can have a few "virtual" firewalls. Like vSYS 1 , vSYS2, vSYS3. If there is a device commit running on one of the vSYS then when you try to run one on a different vSYS you get that error. |
|
Network settings
Device config You select to apply a template on a device or devices. |
|
There is a tag you can add to the devices.
Normal FIPS compliant CC government compliance. Then you choose it too on the template. In order to become applies the TAG on the template must match the one on the firewall. This allows you to set up for example a FIPS template that will apply only to your FIPS firewalls. |
|
After you add a template it will add a TAB for them.
TEMPLATE Network/|/ Device |
|
As you recall this is the template workflow.
Either assign devices then create it Or create it then assign it to devices. |
|
Push the config to the devices.
|
|
You can remove a setting from a template
by clicking the remove X thing. |
|
Select TEMPLATE
Then apply it on the devices or "commit" it. |
|
Icon changes to override Green and Orange
when you change something to make it different from the template. |
|
ADMIN tools
|
|
So devices will send logs
All the logs will be aggregated. Based on the aggregated logs and logs you can create reports for managers. You CAN'T forward logs from a log collector or a panorama to a third party device. You CAN forward them to 3rd party from the firewall. | |
Sending logs to SNMP
SYSLOG this is from the firewall itself. |
|
Generate log is when the action happened.
Receive is when it arrived at the panorama. So there might be a delay. |
|
Data is send to the ACC and dashboard.
The dashboard shows health. The ACC will show you details. |
|
Select Panorama or device context.
Select the time frame. |
|
Summary reports will give you charts.
You can look at them to try to get patterns. |
|
Panorama reports for you.
Ondemand or scheduled. SAev or expert as CSV. You can schedule a report and email it. User Activity is used for summary of URL. PDF Summary will aggregate a number of smaller PDF reports into a big one. Custom reports allows you to filter. |
|
This is the screen where you export reports.
CSV XML Application , traffic, threat, URL Then summary of the above. |
|
This is the user report.
You can select a specific user when generating the report. |
|
This is for creating a custom report using
a custom string. You can also use TEMPLATES to start you off. |
|
Panorama >>device deployment - license
Will allow you to see the licenses and when they are set to expire. This allows you to quickly view and purchase the necessary licenses to keep secure. |
|
Panorama >>device deployment - dynamic updates
allows you to download and install updates centrally you can select to upload to device or upload and install then reboot |
|
Palo Alto best practice is to have one
Collector for every group of devices. If you have two or more collectors a hash will decide where to store the data. This is only needed if more than 4TB of logging. This does not replace SIEM |
|
If you are running version 4 firewalls
then they can't send the logs to the log collector. They will send it to Panorama that can then forward it to the log collector. |
|
On a panorama VM you can use
the space on the VM by adding a 2TB storage. This will make it redundant. You can also mount an NFS Share and store it outside of the VM. NFS will be mounted on the active device only. |
|
Request system logger-mode logger will make it a collector.
Request system logger-mode panorama will make it both a manager and a logger. >show system info |match logger_mode > logger_mode : TRUE is a dedicated. |
|
This helps determine the logging rate.
You can also see the statistics. This will allow you to plan for growth. |
|
Similar to the panorama statistics you can look at the Default collector group statistics.
|
|
You can change retention settings.
This will affect how much data is being logged to the collectors. |
|
Another view of the log collection.
Pan 4.0 goes to panorama. Pan 5.0 can go to log collectors if needed. 50000 per second if you have more then you need to add new collectors or change the amount of logging. |
|
You add disks in pairs.
You format them, which can take 2 hours. Palo alto disks. |
|
show system raid detail If a disk fails. request system raid add disk force no-format. The no-format is so the old data won't be overwritten. |
|
This is the Panorama HA pair.
They talk over the management port. TCP port 28 encrypted 2869 when not encrypted. |
|
So to enable HA click the checkbox.
Then put the IP of the other Panorama. Encryption enabled will encrypt the data. You will need to import the HA key for encrypted. Panorama > Certificate management > certificates. |
|
If you enable PREEMPTIVE
then the primary can take back the role when it is powered back up. If you don't the other one will remain primary till he fails. |
|
Path monitoring will ping an IP to see it is alive.
|
|
the HA status will monitor the
HA between the devices. If something is wrong you will get a RED LED. usually versions or mismatch |
|
On version PAN 5.0 panorama
does backup of the changes. Then you can schedule panorama to export the backups to a share. |
|
You can push versions of the OS to the firewalls.
|
|
To move Panorama from one device to another.
Use the Export snapshot. Commit it to the new device with the same IP and check the firewalls can be managed from the new panorama. |
|
Configure management IP
retrieve licenses On panorama run CLI to swap serial. Build the device Import config. |
|
If the serial has changed then you need to search the logs with both serials
as you can't change past data. |
|




























































































Thanks a bunch for this! :-)
ReplyDeleteThanks a lot for the Panorama study tour ... !!
ReplyDeleteThanks for your post !
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteI had to stop reading at 'Palo Alto is not even stateful. It simply cares about APPLICATIONS.'
ReplyDeleteIf you can't even get that basic part right, what else in your guide is wrong?
Palo Alto runs APP-ID which works based on applications.
DeleteNot the session and port state of the past.
So at the time the guide was written. Palo Alto marketing refused applying the "stateful" firewall term in their documentation.
Palo alto is a NGFW next generation firewall according to marketing and guidelines from them.
Up to you if you want to read the guide.
It's not perfect but you won't find much on the subject elsewhere.
thanks so great information defined on short notes.
ReplyDeleteNice Blog
ReplyDeleteCertified Paloalto Partner
Fortinet Certified Partner
thankz
ReplyDeleteCertified Paloalto Partner
CISCO Certified Partner
ReplyDeleteFortinet Certified Partner
Certified Paloalto Partner
CISCO Certified Partner services in bangalore
Fortinet Certified Partner services in bangalore
Certified Paloalto Partner services in bangalore
CISCO Certified Partner
ReplyDeleteFortinet Certified Partner
Certified Paloalto Partner
CISCO Certified Partner services in bangalore
Fortinet Certified Partner services in bangalore
Certified Paloalto Partner services in bangalore
Network Security Projects for CSE
ReplyDeleteJavaScript Training in Chennai
Project Centers in Chennai
JavaScript Training in Chennai
perde modelleri
ReplyDeletesms onay
mobil odeme bozdurma
nft nasıl alınır
ankara evden eve nakliyat
Trafik sigortasi
dedektör
web sitesi kurma
Ask kitaplari